Authorization can be done without others rummaging through your data
Are you concerned that your data isn’t truly secure?
Do you worry that data from one domain is making it to another and THEN being compromised?
Are you tired of having to run yet another pen test, juuuust in case?
Think Differently About Authorization Management:
Never breach a boundary
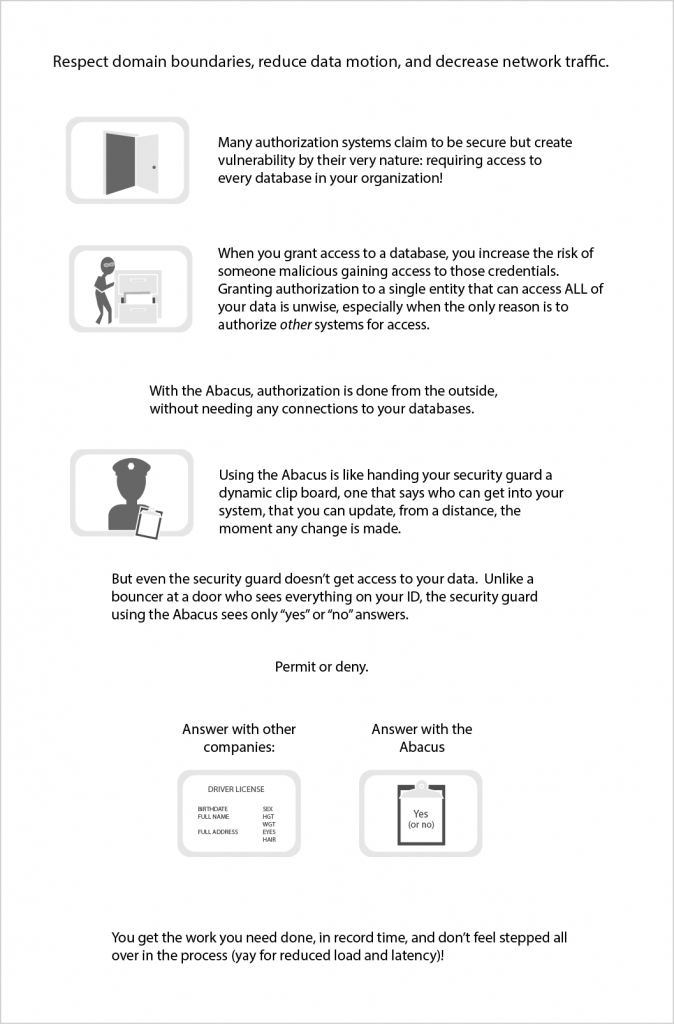
With our approach to authorization you don’t need to grant database access to others!
We’ll help you reduce data motion in your network AND save you money by reducing your IT costs, all while having your data protected.
